The Second Brain for Your Digital Workforce
Agent Memory transforms your automations from simple task executors into intelligent, context-aware digital employees that remember everything about your business, preferences, and relationships between platforms. Think of it as the difference between a temp worker who needs instructions for everything and a seasoned employee who knows your business inside out.Understanding Agent Memory
Memory Architecture
The Six Pillars of Agent Intelligence
Platform Preferences
How you like to use each platform, your settings, and personal configurations
Platform Functionality
How different platforms work, their quirks, and navigation patterns
Relationships
How platforms connect to each other and data flows between them
Business Context
Your company information, products, services, and strategic goals
Personal Style
Your communication tone, writing style, and decision patterns
Process Knowledge
Policies, procedures, compliance requirements, and best practices
Memory Categories
Structured Knowledge Organization
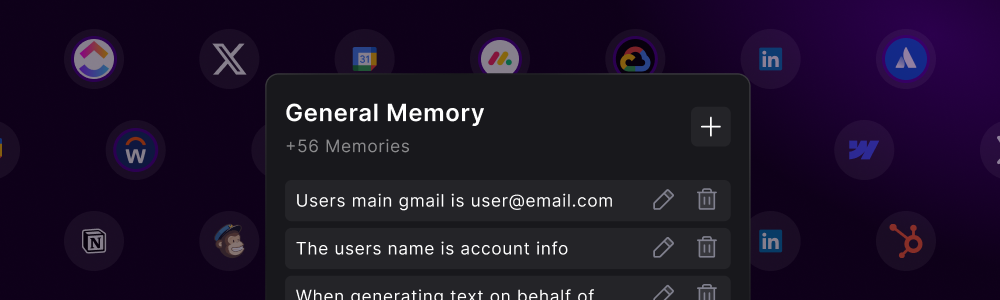
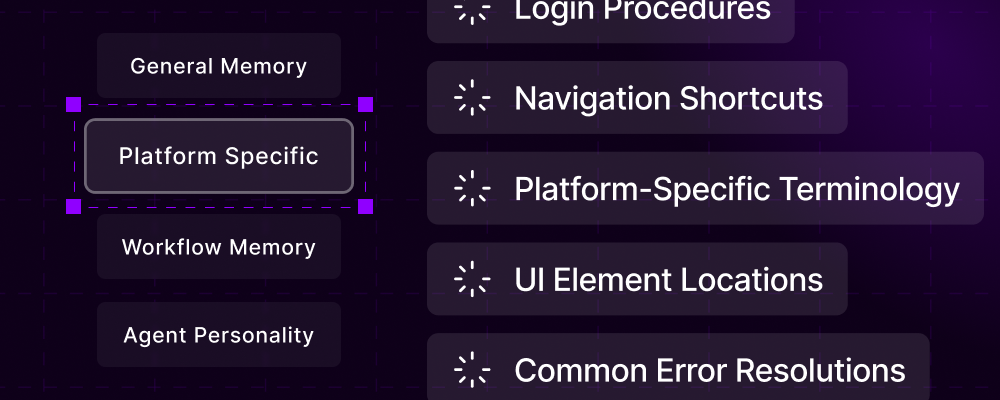
- General Memory
- Platform-Specific
- Workflow Memory
- Agent Personality
Universal Knowledge BaseThe default memory section that applies across all workflows:
- Company information
- Brand guidelines
- Common procedures
- Default preferences
- Universal shortcuts
- Cross-platform rules
- “Our company fiscal year ends in March”
- “Always use British spelling for UK clients”
- “CEO prefers bullet points over paragraphs”
- “All reports should include an executive summary”
How Memories Enhance Workflows
From Basic to Brilliant Automation
Context Injection at Runtime
Context Injection at Runtime
Smart Memory RetrievalWhen a workflow executes, the system automatically:
- Analyzes the current task and platform
- Retrieves relevant memories from all categories
- Injects context into the agent’s decision-making
- Prioritizes memories by relevance and recency
- Updates execution strategy based on knowledge
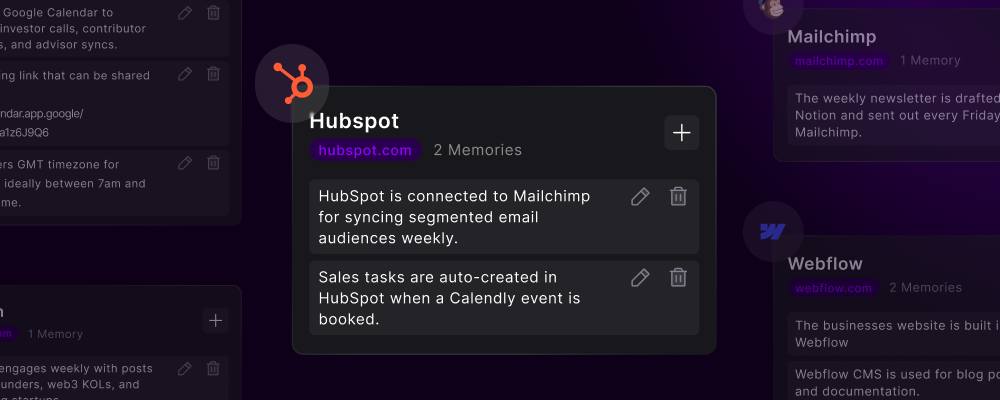
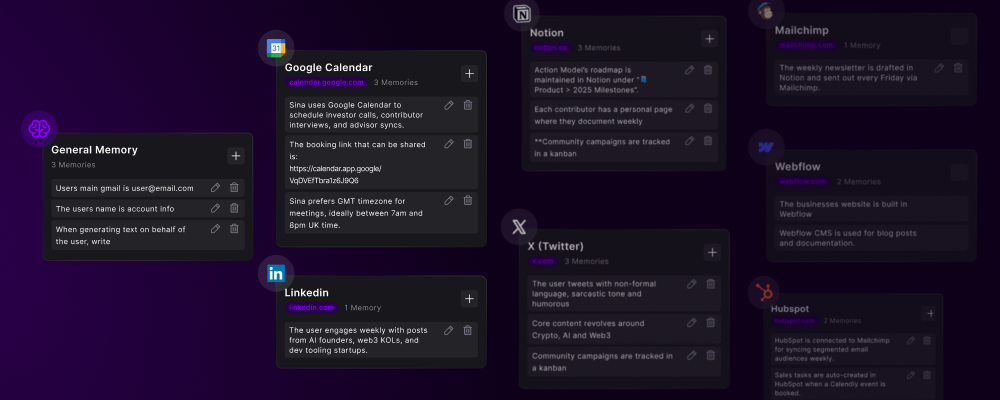
Cross-Platform Intelligence
Cross-Platform Intelligence
Connected Knowledge GraphMemories create relationships between platforms:
- “Customer in Salesforce = @handle on Twitter”
- “Project Alpha in Asana = Folder X in Google Drive”
- “Invoice #1234 in QuickBooks = Contract ABC in DocuSign”
- “Lead from LinkedIn = Contact in HubSpot”
Learning from Experience
Learning from Experience
Continuous ImprovementEvery workflow execution can update memories:
- Successful patterns are reinforced
- Errors create new warning memories
- Optimizations are automatically noted
- User feedback becomes permanent knowledge
Personalization at Scale
Personalization at Scale
Unique Digital DNAMemories make each agent unique to your business:
- Industry-specific terminology
- Company-specific processes
- Personal communication style
- Custom platform configurations
- Unique workflow patterns
Creating and Managing Memories
Three Ways to Build Intelligence
Manual Memory Entry
Direct Knowledge InputAdd memories through the dashboard:
- Navigate to Memory section
- Choose category (General/Platform/Workflow)
- Enter memory in natural language
- Tag with relevant keywords
- Set importance level (Low/Medium/High/Critical)
Passive Learning
Let Your Agent Observe and LearnLet your Agent observe your screen as you work. Over time, it absorbs your patterns, preferences, and processes without explicit training:
- Detects repeated patterns
- Notes platform-specific behaviors
- Learns navigation preferences
- Captures decision criteria
- Records error resolutions
Memory Types and Formats
Structured Knowledge Storage
- Factual Memories
- Procedural Memories
- Conditional Memories
- Relational Memories
Static InformationConcrete facts that don’t change:
- Account numbers
- API endpoints
- Company policies
- Legal requirements
- Product specifications
Memory Security & Privacy
Protecting Your Digital Intelligence
Encryption at Rest
- AES-256 encryption for stored memories
- Separate encryption keys per organization
- Hardware security module protection
- Zero-knowledge architecture
Encryption in Transit
- TLS 1.3 for all memory transfers
- Certificate pinning
- Perfect forward secrecy
- Memory isolation between agents
Access Control
- Role-based memory access
- Memory compartmentalization
- Audit logging for all access
- Granular permission settings
Data Sovereignty
- Choose memory storage region
- GDPR/CCPA compliant
- Right to deletion
- Data portability
Memory Analytics
Understanding Your Knowledge Base
Memory Intelligence Dashboard: Track how memories improve automation performance and identify knowledge gaps.
| Metric | Description | Optimal Range |
|---|---|---|
| Memory Utilization | How often memories are accessed | 70-90% |
| Knowledge Coverage | Platforms with memory data | >80% |
| Memory Accuracy | Successful memory applications | >95% |
| Growth Rate | New memories per week | 50-200 |
| Relevance Score | Memory-to-task matching | >85% |
Real-World Memory Applications
Example 1: Customer Service Excellence
- Memory Setup
- Impact
Customer Knowledge Base:
Example 2: Financial Operations
- Memory Setup
- Results
Financial Process Knowledge:
Memory Best Practices
Start with Core Knowledge
Start with Core Knowledge
Build your memory foundation systematically:
- Company basics: Mission, values, key information
- Platform access: Login procedures, navigation
- Common tasks: Frequent workflow patterns
- Business rules: Policies, procedures, compliance
- Relationships: Cross-platform connections
Regular Memory Maintenance
Regular Memory Maintenance
Keep memories accurate and relevant:
- Review memories monthly
- Remove outdated information
- Update platform changes
- Consolidate duplicate memories
- Archive historical memories
Memory Naming Conventions
Memory Naming Conventions
Use clear, searchable memory titles:
- ✅ “Salesforce: Create opportunity from lead”
- ❌ “SF opp process”
- ✅ “Client ABC Corp: Prefers formal communication”
- ❌ “ABC notes”
Security Classifications
Security Classifications
Classify memories by sensitivity:
- Public: General business information
- Internal: Company procedures
- Confidential: Client data, strategies
- Restricted: Passwords, API keys
The Future of Agent Memory
Coming Soon
Memory Networks
Agents sharing knowledge across organizations (with permission)
Semantic Search
Natural language memory queries: “How do we handle refunds?”
Memory Templates
Pre-built memory sets for common industries and use cases
AI Memory Generation
Automatic memory creation from documentation and wikis
Getting Started with Memory
The Compound Effect: Every memory you add makes all future automations smarter. This is how you build a competitive advantage that compounds over time—your agents become uniquely intelligent about YOUR business.
Memory Templates
Browse pre-built memory sets
Best Practices
Learn memory optimization
Security Guide
Understand memory protection
Agent Memory: Where knowledge becomes permanent, intelligence becomes cumulative, and your digital workforce becomes irreplaceable. Build once. Remember forever. Evolve continuously.